D2D, V2V, V2I
D2D
Operator Controlled D2D Communication and Challenges:
Overview:
- Different from traditional device-to-device communication technologies such as Bluetooth and WiFi-direct, the operator controls the communication process to provide better user experience and make profit accordingly
- Up to now, D2D is not in 3GPP, because the D2D function was only envisioned as a tool to reduce the cost of local service provision, which is fractional according to the operators’ current market statistics. However it is changing for several new market trends:
- Context-aware applications as value added services provided by Operator
- Cell Phone of a owner can be the hub for consumer electronic devices to connect to their networks; D2D from these devices to Cell Phone
- Disadvantages of traditional D2D technologies like Bluetooth and WiFi-direct (although they are free) compared to Operator controlled cellular network:
- Require manual pairing
- Interference is uncontrollable on the crowded 2.4GHz unlicensed band
- Cannot guarantee Security and QoS unlike a cellular network
Operator Controlled D2D Modes:
Controls - access authentication, connection control, resource allocation and lawful interception.
- Fully Controlled D2D Mode:
- Full control including control plane functions, e.g., connection setup and maintenance, and data plane functions, e.g.,resource allocations
- Share cellular licensed band
- Dynamic resource allocation like for normal cellular or semi-static dedicated pool for all D2D connections
- Loosely Controlled D2D Mode:
- Perform access authentication
- Communication after is over unlicensed band (Bluetooth etc.,) or dedicated carrier on licensed band
- Charged per month and can disable D2D anytime
Use Cases and Business Models:
- Peer-to-Peer:
- Local Voice Service: Offload local voice traffic.. e.g., in same supermarket
- Local Data Service: Friends content sharing, multi-player gaming, local multicasting (shops advertise), machine-to-machine (e.g., phone to tv share), context-aware application (e.g., "check-in" at venues earn awards)
- Advantages of operator controlled D2D services ("pay-for-what"):
- Pay for Identity - Loosely controlled D2D to link phone number for WiFi Identity to share between devices
- Pay for QoS and Security - Fully controlled D2D for high QoS and/or Security
- Pay for context information - that operator has a lot of to leverage to
- Relay:
- UE as Gateway to Sensor Networks:
- Cell phone as gateway for Sensors (M2M devices) on home devices, cars, or on-body healthcare devices
- Advantages of operator controlled D2D services ("pay-for-what"):
- Pay for management - non-cellular devices managed in operator subscriber database and associated to owner's cellular device; manage profile of owner and device specific access policies; meter data for sensors behind phone/gateway
- Pay for QoS and Security - Fully controlled D2D for high QoS and/or Security (for ex., sensors for life care or security)
- UE cooperative Relay:
- UE as relay of another's information - risky and extra power consumption just for relay; not incentive enough for users
- Future studies on achieving transmit diversity, multi-antenna transmission and network coding etc., thru cooperation
Technical Considerations in RAN:
- Spectrum:
- Unlicensed band:
- Using loosely controlled D2D; however uncontrolled interference
- FDD licensed band:
- UE to add additional Rx/Tx chain; more cost
- TDD licensed band:
- No additional Rx/Tx chain; share resources or allocate dedicated carriers
- Guard band between TDD and FDD:
- Half-duplex FDD in guard band
- Cost-efficient still controlled
- Power Control, Resource Allocation and Interference Management:
- Distributively determined by UEs themselves:
- Dedicated resources assigned statically (loosely controlled) or semi-statically (fully controlled) so that no interference (e.g., FlashLinQ)
- Centrally performed by eNodeB (fully controlled):
- Dedicated resources or share with cellular users
- Emphasis for optimal performance on
- Resource Sharing Mode Selection - D2D communication or not for a user pair; dedicated or shared with cellular users
- Resource Allocation
- Power Control Algorithms
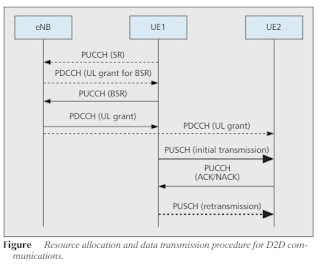
- Centralized resource allocation approach is explained in above Figure (proposal):
- Assumed UE1 and UE2 already established D2D connection and UE1 has data wait to be sent to UE2
- Resource allocation for most part looks similar to LTE, except:
- Channel status of UE1<->UE2 link by periodic or aperiodic CQI reports from them thru PUCCH (estimated from SRS transmitted between them) to eNodeB
- Then eNodeB notifies the resource allocation to both thru PDCCH, coded with C-RNTI
- Two separate PDCCHs with separate C-RNTI's (uplink grant to UE1 and downlink grant to UE2) or
- One PDCCH with C-RNTI of UE1 (here UE2 needs to know UE1's C-RNTI then, during D2D connection establishment); reduce signalling overhead but increase the blind decoding attempts for the UEs
- Then UE1 transmits data to UE2 on allocated resources
- since it is D2D link, there shall be no difference link uplink or downlink, so better to use PUSCH both sender and receiver; else (UE1 sends uplink) UE2 needs to estimate downlink channel by detecting CRS and UE1 doesn't transmit CRS (only eNodeB does it); need devices to have uplink reception ability also for this
- Then UE2 sends ACK/NACK on PUCCH
- Reserve specific resources for D2D PUCCH or
- Dedicated carrier for D2D ACK/NACK different from cellular ACK/NACK
- No core network resources needed for D2D traffic; however, need a way to identify Application data passing thru PDCP to lower layers as to be sent to another device and not to eNodeB
- Peer discovery, Paging and Connection Establishment
- This is done of course prior to resource allocation and data transmission
- Peer Discovery:
- Centralized approach:
- MME or PGW determines it is better to setup D2D connection
- Informs eNodeB to request measurements and decide on D2D communication
- Distributed approach:
- UE broadcasts it identity for peers to aware of its existance
- Flexible, but operator cannot forbid illegal users listening on licensed band
- Paging and Connection Establishment:
- Fully controlled D2D:
- Normal as LTE, but need to inform to each UE of peer's C-RNTI, SRS configuration, ciphering key etc.,
- Loosely controlled D2D on licensed band:
- Once operator allows D2D connection setup, then a direct D2D paging for connection setup without eNodeB
- Loosely controlled D2D on unlicensed band:
- After authentication, then use traditional D2D for data transmission
Conclusion:
The operators still face several challenges in providing such a D2D solution that can address the below two “contradicting” objectives simultaneously:
- Provide better user experience and make profit accordingly, yet..
- Low-cost to compete with traditional free D2D communications
References
2. https://www.researchgate.net/publication/254061548_Operator_controlled_Device-to-Device_communications_in_LTE-Advanced_networks
3. http://users.ece.utexas.edu/~shakkott/Pubs/flashlinq-full.pdf (for peer-to-peer discovery)
4. http://www.eenewsautomotive.com/design-center/why-80211p-beats-lte-and-5g-v2x
5. http://www.d.umn.edu/ee/cvrl/documents/V2V%20Assisted%20system.pdf
6. https://arxiv.org/ftp/arxiv/papers/1502/1502.00143.pdf
3. http://users.ece.utexas.edu/~shakkott/Pubs/flashlinq-full.pdf (for peer-to-peer discovery)
4. http://www.eenewsautomotive.com/design-center/why-80211p-beats-lte-and-5g-v2x
5. http://www.d.umn.edu/ee/cvrl/documents/V2V%20Assisted%20system.pdf
6. https://arxiv.org/ftp/arxiv/papers/1502/1502.00143.pdf


Comments
Post a Comment